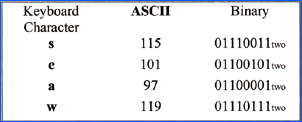
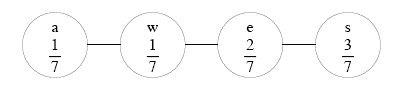
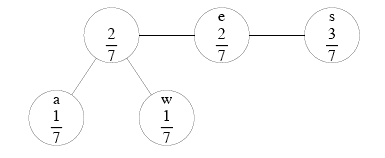
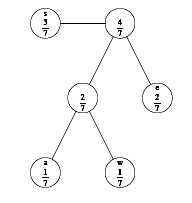
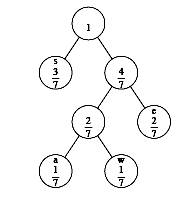
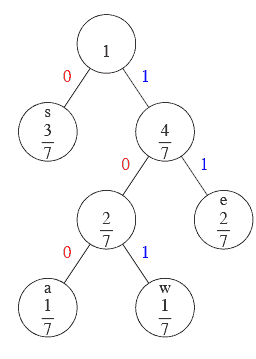
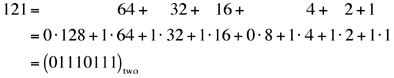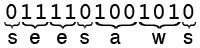|
References
[1] R. C. Gonzalez and R. E. Woods, "Digital Image Processing", 2nd ed., Prentice Hall, 2002.
[2]
C. K.
Chui, “An introduction to wavelets ”, Academic Press, San Diego, 1992.
[3]
W. Dahmen,
Multiscale problems and methods in numerical simulations, CIME
Summer
Course, 2001
< http://www.igpm.rwth-aachen.de/dahmen/cime/
>.
[4]
I. Daubeschies,
“Ten lectures on wavelets ”, SIAM, Philadelphia, 1992.
[5]
Mark W. Drew and Ze-Nian Li, "Fundamentals of Multimedia", Prentice
Hall, 2003.
[6]
A. Gelb
and E. Tadmor, Detection of edges in spectral data, To appear in
Applied
and Computational Harmonic Analysis.
[7]
S.
Mallat, “A wavelet
tour of signal processing ”, Academic Press, 1998.
[8] E.
J. Candes, Harmonic analysis of neural
networks,
Appl.Comput.Harm.Anal., 6 (1999), 197-218.
|